45+ Zero Trust Architecture Diagram
Input and cooperation from. Rose Oliver Borchert Stuart Mitchell Sean Connelly Abstract Zero trust ZT is the term for an.
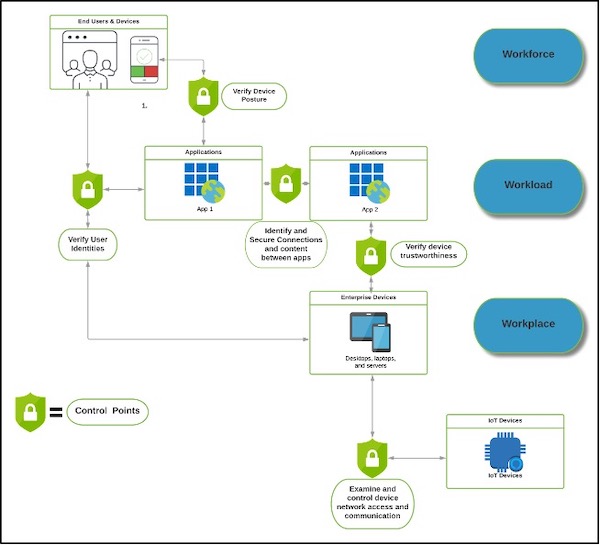
The Zero Trust Approach To Important Control Planes Duo Security
Presenters Amit Kapoor - Integrity Security Services.
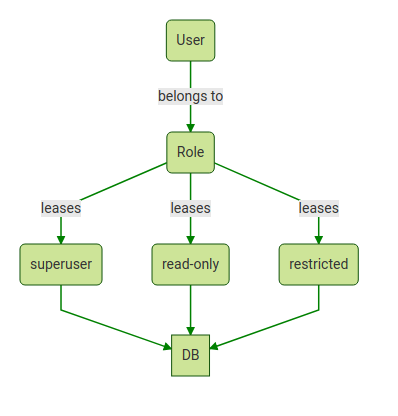
. Web 21 Abstract 22 Zero trust is a set of cybersecurity principles used when planning and implementing an enterprise 23 architecture. Use Lucidchart to visualize ideas make charts diagrams more. Ad Explore Microsoft Protection Policies That Help Manage and Defend Data Across Devices.
Ad Lucidcharts diagram software is quick easy to use. Web This document provides a quick overview of the NIST Risk Management Framework NIST RMF and how the NIST RMF can help in developing and. Web Before we examine zero trust architecture in more detail lets distinguish between these two interrelated terms.
Share to Facebook Share to Twitter. Get our Enterprise Architecture Framework poster for free. A zero trust architecture ZTA is a design that supports zero.
Web Zero trust network access ZTNA is the application of zero trust architecture which Gartner defines as the creation of an identity- and context-based logical access. Web The Zero Trust strategy is more difficult to breach because it launches repeated authentication requests before granting any user access. Empower Your Users to Work More Securely Anywhere and Anytime on Any Device.
Web Zero Trust Architecture ZTA also known as Zero Trust Security Model or Zero Trust Network Access ZTNA is a shift in approach to security whereby access is. Web Zero Trust ZT requires designing a consolidated and more secure architecture without impeding operations or compromising security. End-to-end governance Siloed systems introduce risk.
Web This article outlines what Zero Trust is how Zero Trust works the five core principles of Zero Trust and the stages of implementing Zero-Trust security. Web Zero Trust Architecture Initiative Tenets of Zero Trust All enterprise systems are considered resources. Ad Download your complimentary copy of The Essential Guide to Zero Trust.
Discover how a data-first approach to security helps build zero trust architecture. Web Understand the Zero Trust security model learn about the principles and apply the Zero Trust architecture using Microsoft 365 and Microsoft Azure services. NIST Special Publication 800-207 defines zero trust as a set of cybersecurity principles used when planning and implementing an enterprise.
Discover how a data-first approach to security helps build zero trust architecture. Web Zero Trust Software Registry Architecture. Web The following table shows how Zero Trust Frameworks map to the Cisco Zero Trust Framework.
Web What Is Zero Trust Architecture. Instead Zero Trust authenticates access to an organizations whole. The enterprise ensures all owned systems are in their most.
Use Lucidchart to visualize ideas make charts diagrams more. ZTA addresses these challenges by redefining the overall architecture removing the concept of a trusted zone inside a. Ad Lucidcharts diagram software is quick easy to use.
Web A more secure future may require a zero-trust architecture in which users must prove their authenticity each time they access a network application or data. Web Zero trust is a set of cybersecurity principles used to create a strategy that focuses on moving network defenses from wide static network perimeters to focusing more narrowly. This architecture guide is focused on the Cisco Zero Trust.
Ad Learn how to bring EA to the next level with a lean EA approach. Web Abstract NIST Special Publication 800 -207 defines z ero trust as a set of cybersecurity principles used when planning and implementing an enterprise architecture. Web Up to 20 cash back ZT is a concept but the basics of a ZT framework have been defined by the National Institute of Standards and Technology NIST and by analyst firms such as.
Web Zero Trust Architecture Published August 10 2020 Author s Scott W. Ad Download your complimentary copy of The Essential Guide to Zero Trust. Web Key features of Zero Trust architecture include.

Zero Trust Security Architecture Overview Developer Com
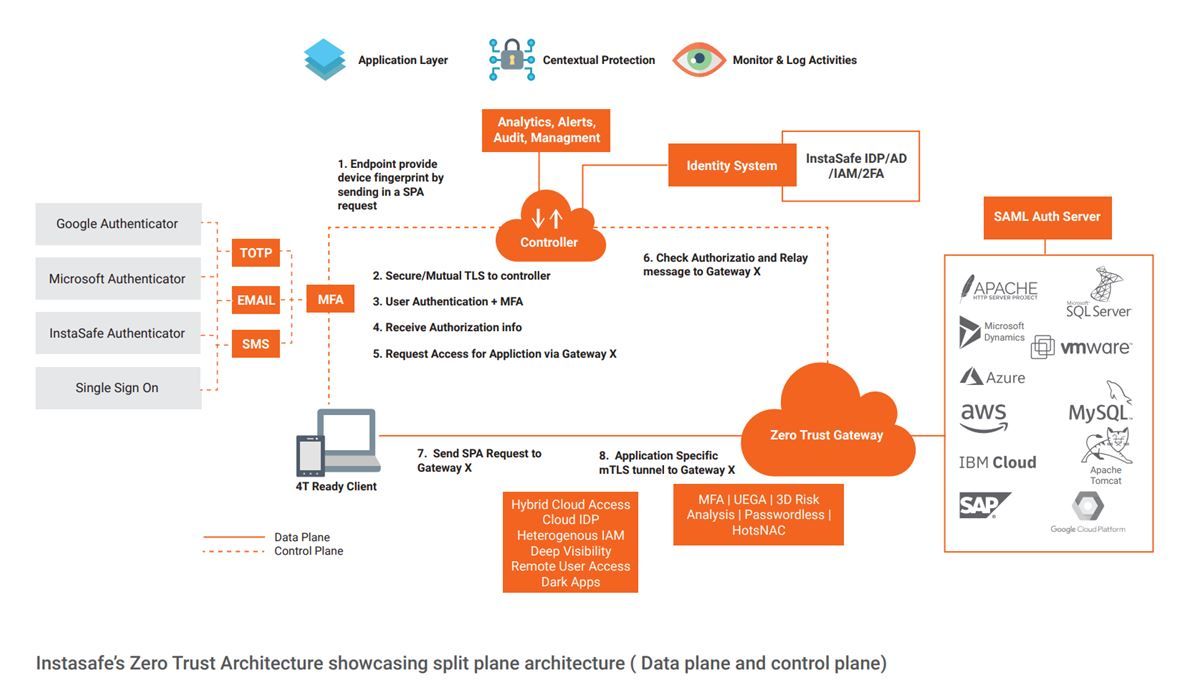
Choosing The Right Zero Trust Architecture
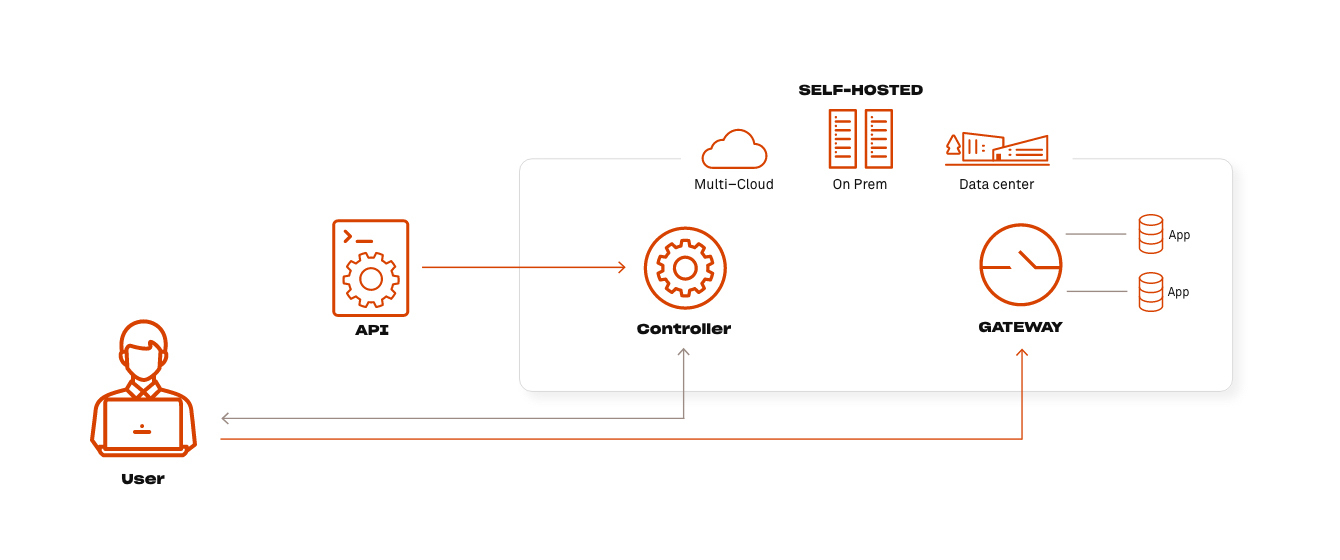
Appgate Ztna Architecture Zero Trust Architecture Ztna
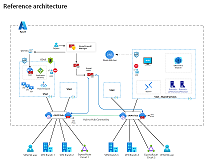
Zero Trust Illustrations For It Architects And Implementers Microsoft Learn
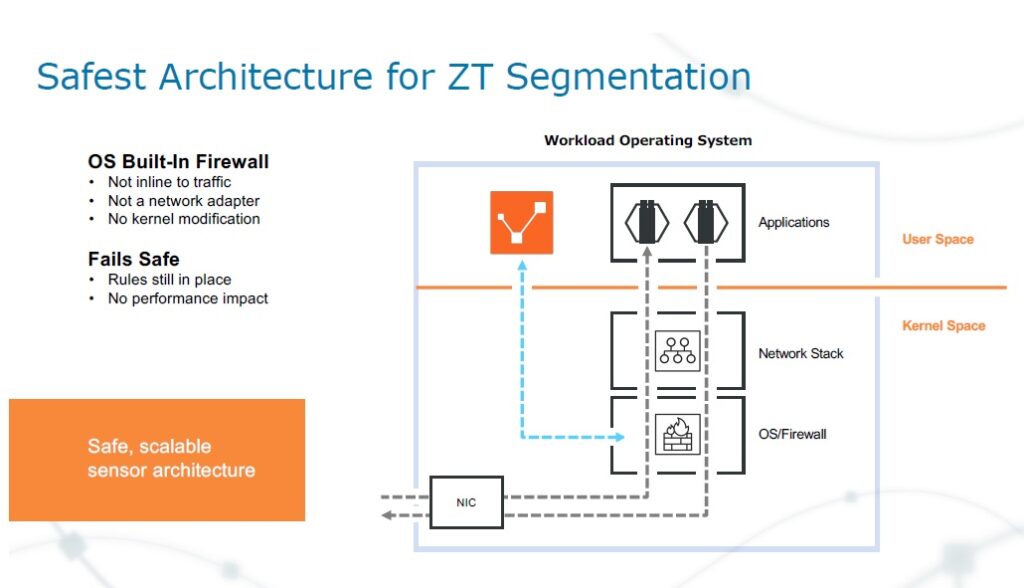
How Zero Trust Architecture Keeps Defence It Assets Secure

Zero Trust Architecture Enhancing Network Security Secureblitz Cybersecurity
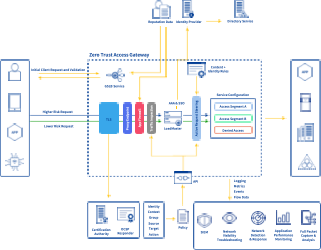
Kemp Zero Trust Access Gateway Architecture Overview Load Balancers Kemp
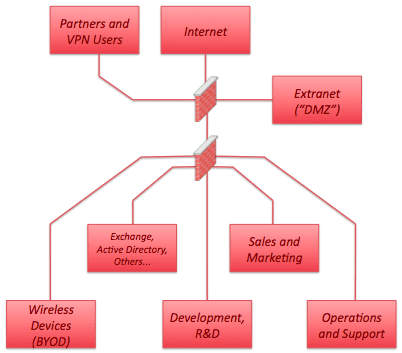
Network Segmentation Segregation And Zero Trust Design
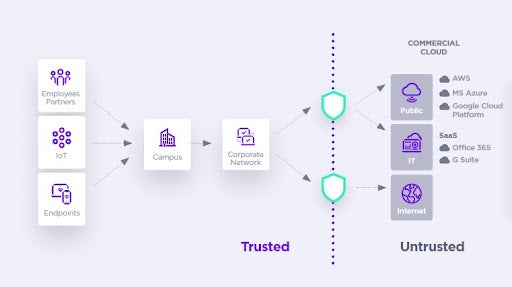
Zero Trust Architecture Explained Sentinelone

How To Think About Zero Trust Architectures On Aws Aws Public Sector Blog
A Roadmap To Zero Trust Architecture
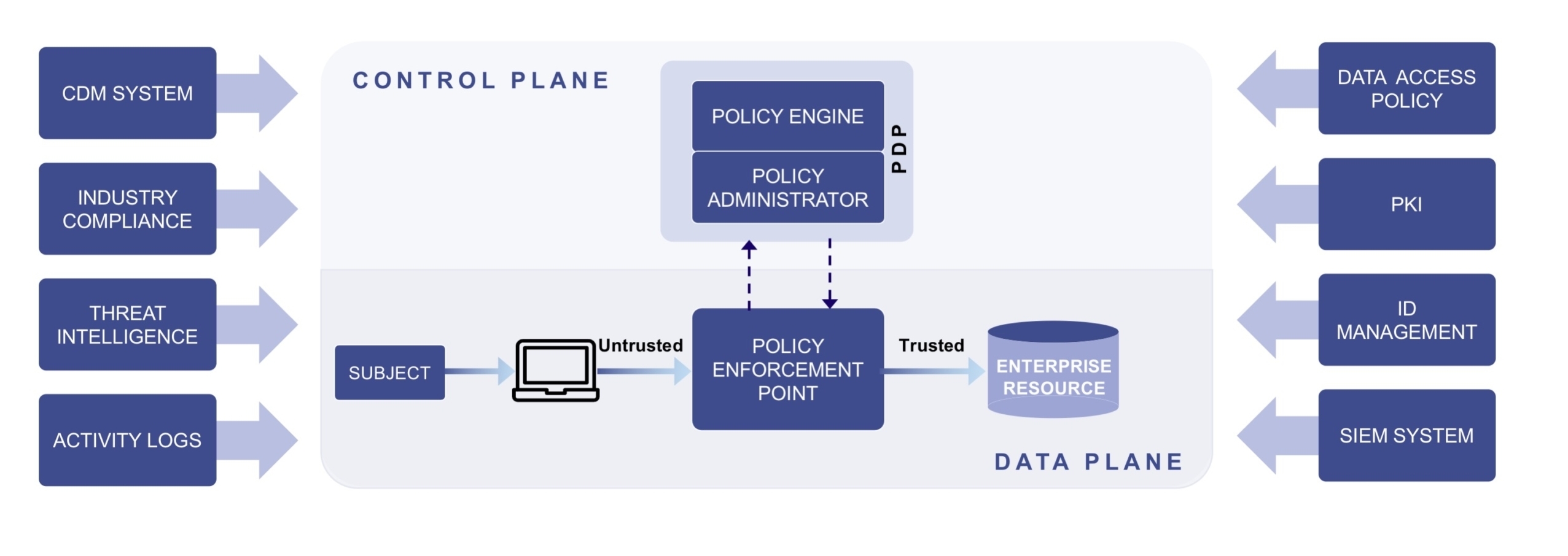
What Is Zero Trust Architecture All About Gadget Access

Is Zero Trust Architecture The Method Of Future Cybersecurity A Fixvirus Blog

Zero Trust Strategy What Good Looks Like Trust Strategies Guidance
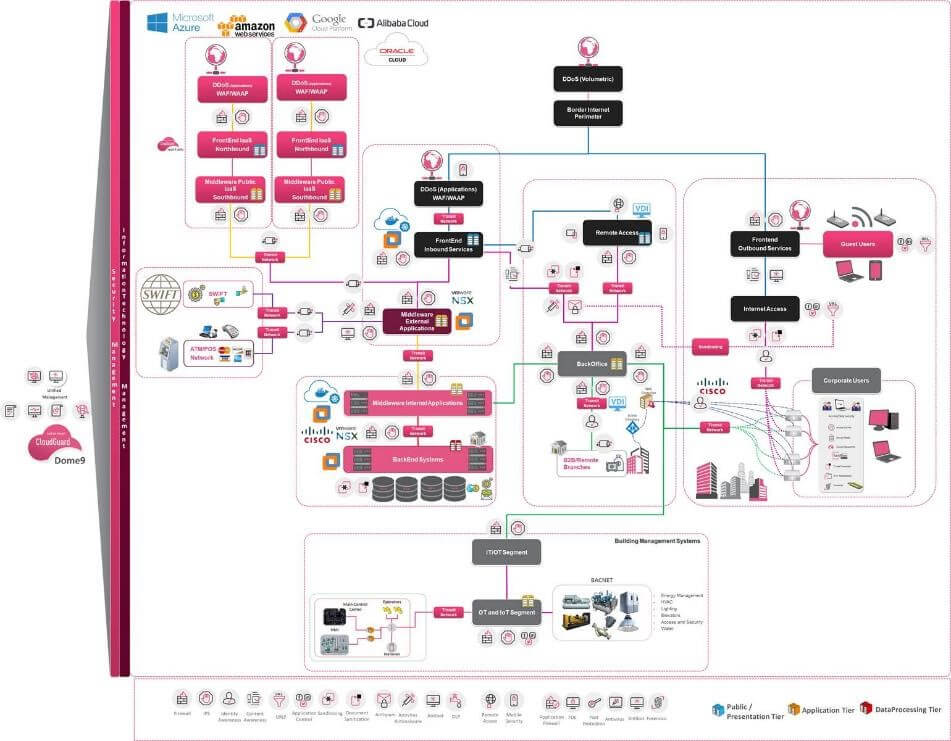
What Is Zero Trust Security And Why Should You Care

Why A Zero Trust Approach To Data Management Rubrik
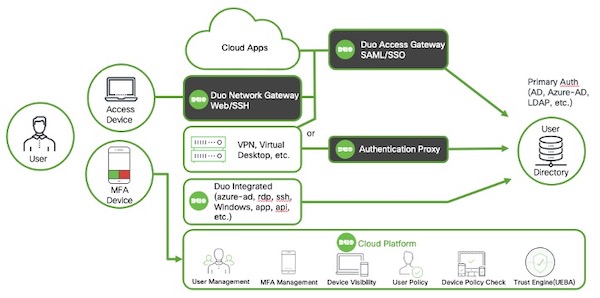
The Zero Trust Approach To Important Control Planes Duo Security